How to Protect Your Website
The first thing to know about securing your website (and in my opinion, the most important thing) is that you are not doing this as an absolute guarantee against malicious attackers.Huge organizations regularly have their websites taken down by DDOS attacks or defaced by hacktivist organizations like the Syrian Electronic Army.In the worst-case scenario, their sites make their users’ Personally Identifiable Information (PII) become vulnerable due to cross site scripting.
What I’m saying is, the security that you enable for your website is more of a sieve than an umbrella. You can deflect big, obvious, and clumsy attacks — the kind comprising up to 97 percent of cyberattacks — but there will always be someone clever and subtle enough to penetrate your defenses. A good cyber-defense will always include a plan for when (not if) your defenses fail.That being said, here are some of the most common attacks against websites — cross site scripting, information leakage, and DDOS attacks — and how to deflect them.
Cross Site Scripting (XSS)
Cross-site scripting is a dangerous problem to have. Unlike vandalism or a DDOS attack, cross-site scripting attacks turn your website into a malware vector, and can compromise your users’ personal information.A common example is this: let’s say that you have a contact form on your website.
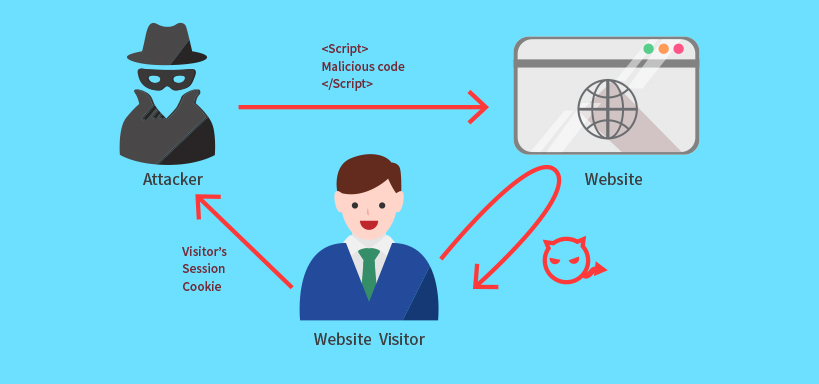
Instead of putting in their name, email, and message, an attacker would write some arcane code-string, and then hit the ‘submit’ button.
If you’re unlucky or un-careful, that string of code then worms its way into your website’s database — it becomes a part of your site.
When a user visits your site, their browser renders all of your content right alongside the attacker’s code. This allows the attacker to do things like record every single one of the user’s keystrokes, thus eventually capturing their username, password, SSN, credit card numbers, and so on.
How do you defend against cross-site scripting?
Much has been written on the subject of preventing cross-site scripting, and the good news is that it doesn’t require buying an expensive security solution.Your website developer can bake in protection against XSS as they build or modify your site.
Essentially, you need to treat all user input into your site as ‘untrusted.’ It could be someone genuinely reaching out to you, or it could be malicious code.Therefore, this data needs to be encoded, or transformed into the sort of text that doesn’t render in a browser, before being added to your database.
Information Leakage
This is one of the most common causes of attacks against websites, and it isn’t even based on a specific software vulnerability.
Do me a favor — when you’re reading this on a desktop, quickly hit F12 on your keyboard. If that doesn’t work, you may need to right-click and hit ‘view source.’ Either way, you’ll end up seeing something like this:
You probably already know what this is, if you’re a developer — it’s the HTML source code for a given webpage. You also know that as you develop a page or a web application, you’re likely to leave comments in that code, indicating the presence of a bug, for example.

Distributed Denial of Service Attacks (DDOS)
I’ve written extensively about DDOS attacks in the past, and they are the worst.
They work on the principle that it’s very easy to crash a website by sending a lot of illegitimate web traffic to it at the same time.
A single user can generate a DDOS attack by spamming DNS traffic. Other times, a hacker uses one or more infected computers that are being controlled remotely in order to accomplish the same task.
A DDOS attack might be for ideological reasons — both the Syrian Electronic Army and the Russian Federation have been tied to DDOS attacks — but mostly the attackers want cold, hard, bitcoins.




